The Solution
NHS Secure Boundary comprises two main technology parts, protecting two types of internet traffic:
- Bi-directional traffic (initiated internally): traffic which is initiated from within the NHS perimeter. For example, the diagram below shows an NHS worker (left) accessing the internet from their NHS device. Their internet activity is protected by PaloAlto and Prisma Access technology.
- Inbound traffic (initiated externally): traffic which is initiated from outside of the NHS perimeter. For example, the diagram below shows a member of the public (right) accessing an NHS hosted site via the internet, from their own personal device. Their data is protected by Imperva Incapsula web application firewall on route to the NHS hosted service.
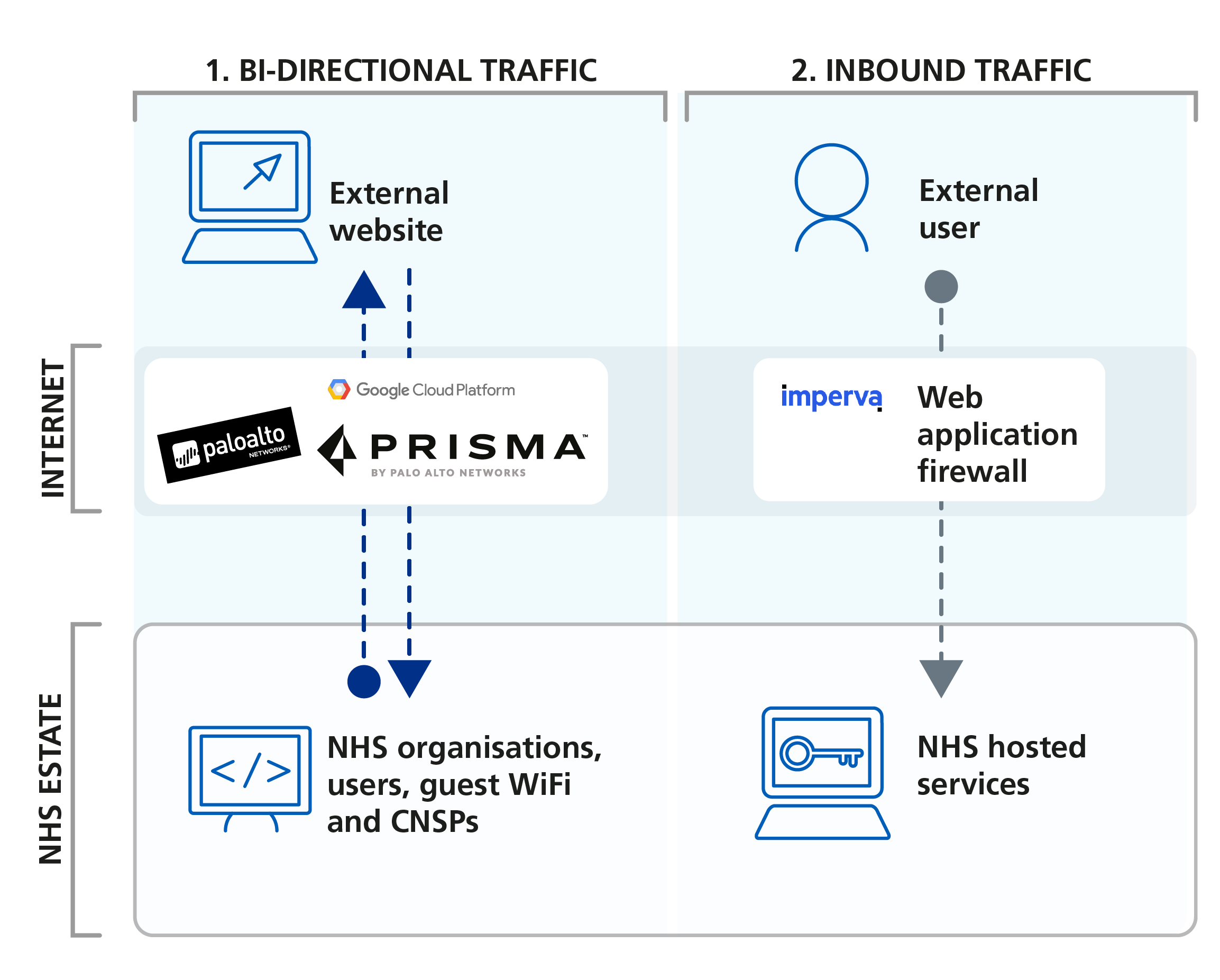
Components of the NHS Secure Boundary Solution
Below are details of the different components which make up this leading-edge NHS Secure Boundary solution.
Palo Alto Prisma Access
This is a software as a service (SaaS) based, modern next-generation firewall (NGFW) capability in the cloud, which can be used by NHS organisations to increase their digital security.
It includes:
- Stateful High Availability (HA) pairs of VM-Series NGFW
- Ability to be hosted across availability zones
- Dedicated firewalls for each tenant
- Bandwidth pool apportioned to tenants based on identified bandwidths
Cortex Data Logging Service
This collates all logs from the firewalls and management platforms within the solution.
It includes:
- Retention of traffic, configuration and system logs for 30+ days in Cortex Data Lakes (CDL’s) accessible by an organisation (logs for six months up to 180 days are accessible via a ticket to the CSF)
- Forwarding of filtered logs to the Cyber Operations, Cyber Security Operations Centre (CSOC), enabling us to monitor cyber events across the NHS estate, and provide rapid protection as incidents and risks emerge
WildFire
Wildfire is a sandboxing platform designed to identify zero-day threats.
It includes:
- File sandboxing for analysis of unknown threats
- Creation of signatures to block malware and block the other behaviours
- Dissemination of threat signatures to all Wildfire users, so detection by one can protect all
- Static and dynamic analysis over multiple operating systems and application versions
Panorama Management Console
Management of the Prisma platform will be done via the central management console, Panorama.
It includes:
- Common Graphical User Interface (GUI) integrated with NHS Mail Single Sign On (SSO)
- Tenant-in-tenant approach to provide global and local control
- Amazon Web Services (AWS) hosted Panorama with additional NGFWs and role-based access control
Imperva Cloud Web Application Firewall (WAF)
This is a SaaS based WAF solution to protect applications from malicious online attacks.
It includes:
- Protection against the most critical web application security risks, such as Structured Query Language (SQL) injection, cross-site scripting, illegal resource access, remote file inclusion
- Multiple capability offerings to meet current and future requirements whilst being cost effective
Feature & Capabilities
Here are some of the features and capabilities offered by the Secure Boundary service.
Uniform Resource Locator (URL) filtering
Monitors and controls access to websites and website categories.
Application ID (APP ID)
Visibility of active applications.
Antivirus
Protects against viruses, worms and trojans, and spyware.
Anti-spyware
Prevents spyware and malware from ‘phoning home’.
Application whitelisting
Protects against potentially harmful applications.
File blocking
Blocks files that are known to carry threats.
Zone and DoS protection
Reduces the portion of the network exposed to potential attack.
Custom signatures
Can be created to detect and block specific traffic.
Intrusion protection (IPS)
Protects against attempts to exploit flaws or gain unauthorised access into NHS systems.
WAF
Protects publicly hosted web services from a wide range of online threats.
USER-ID
Identification of all users on the network enabling enforcement of user and group-based access rules.
Response pages
Customised messages and instructions to users when blocked websites or files are accessed.
QOS/rate limiting
Highest priority activity is not compromised when the network is busy.
Data loss prevention (DLP)
Prevents sensitive information from ever leaving the network.
